Case studies of some of the famous malware. As part of the malware analysis series from the part – 1 we learned what are the…
Latest Posts
FutureUncategorized
Global healthcare would have changed in ways unforeseen by 2039, with the biotech industry that has transformed into something of which individuals in this generation…
Uncategorized
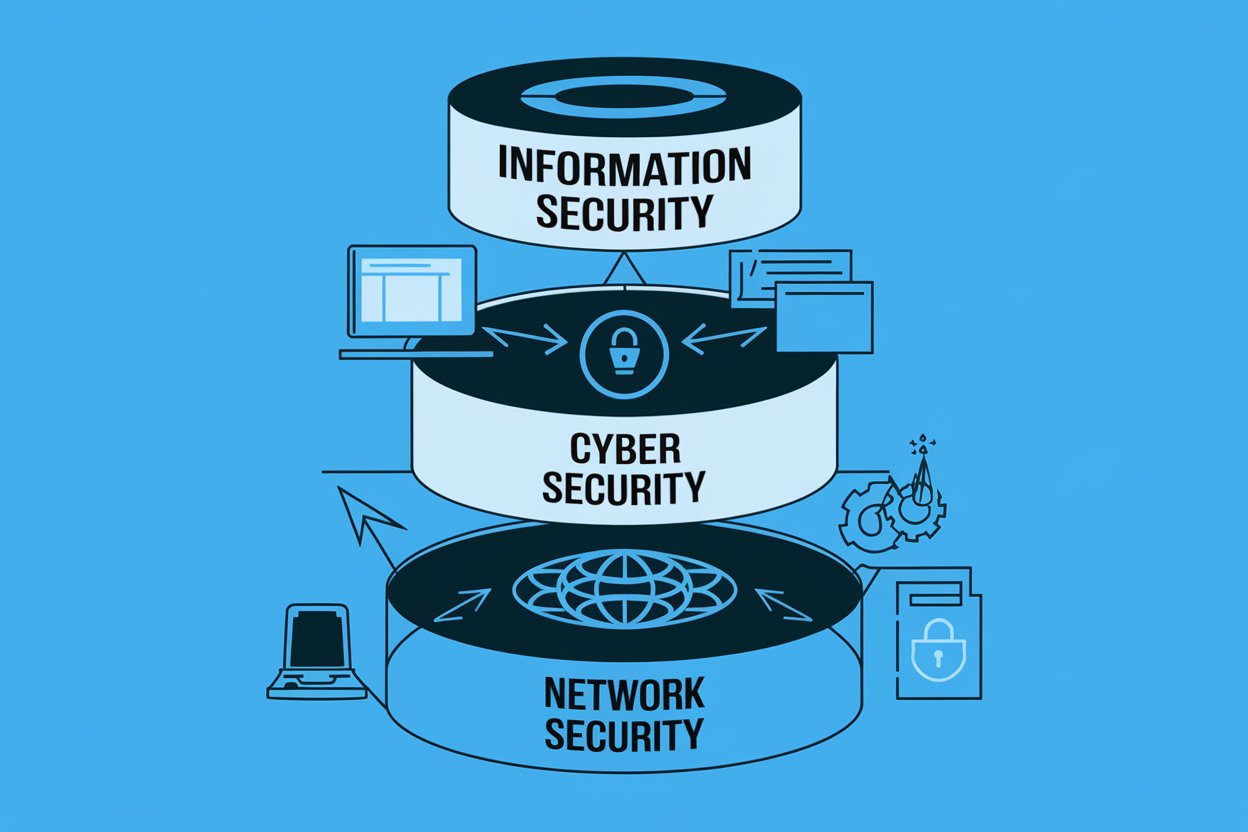
Introduction In today’s digital world, protecting data is crucial for both individuals and businesses. We handle sensitive information every day, from personal details to business…